Modernizing Web Application Security
Modernizing Vulnerability Management with award-winning, game-changing SHIELDING TECHNOLOGY that revolutionizes Web Application Protection making 100% vulnerability mitigation a reality.
Modernizing Vulnerability Management with award-winning, game-changing SHIELDING TECHNOLOGY that revolutionizes Web Application Protection making 100% vulnerability mitigation a reality.
Our streamlined, automated platform operates at an 80-to-1 efficiency ratio–meaning it would take 80 people to achieve the same results as our single, automated, fully managed service.

Web Application Protection developed into a service instead of a product. Our fully managed service combines unparalleled, proprietary and patent-pending shielding technology with world-class cyber security experts, working around the clock to protect your web applications.
Our shielding technology is 10-100X Faster and less expensive than rewriting application code or replacing software.
Protect app-destined traffic through our global shield network.
Conduct 24/7 threat analysis and leading-edge exploitation research.
Utilizing Proprietary advanced shield ti 180k+
Continuous custom shields development, deployment and optimization.
Proprietary managed vulnerability validation and shield correlation.
On-demand mini pen tests.
Real-time analysis and application protection reporting.
Customer portal for access to our processes and world-class expertise.
WAFs cannot fix business logic flaws because they cannot maintain application state. We can. A well-managed WAF needs a skilled engineer on-site. At best, a WAF can only protect up to 30%-50%, still leaving you exposed. We use a best-in-class WAF in our baseline policy with our full managed service, making 100% vulnerability mitigation a reality.

NO RISK | REQUIRES NO CHANGES TO NETWORKS OR APPLICATIONS | IT'S UNAUTHENTICATED
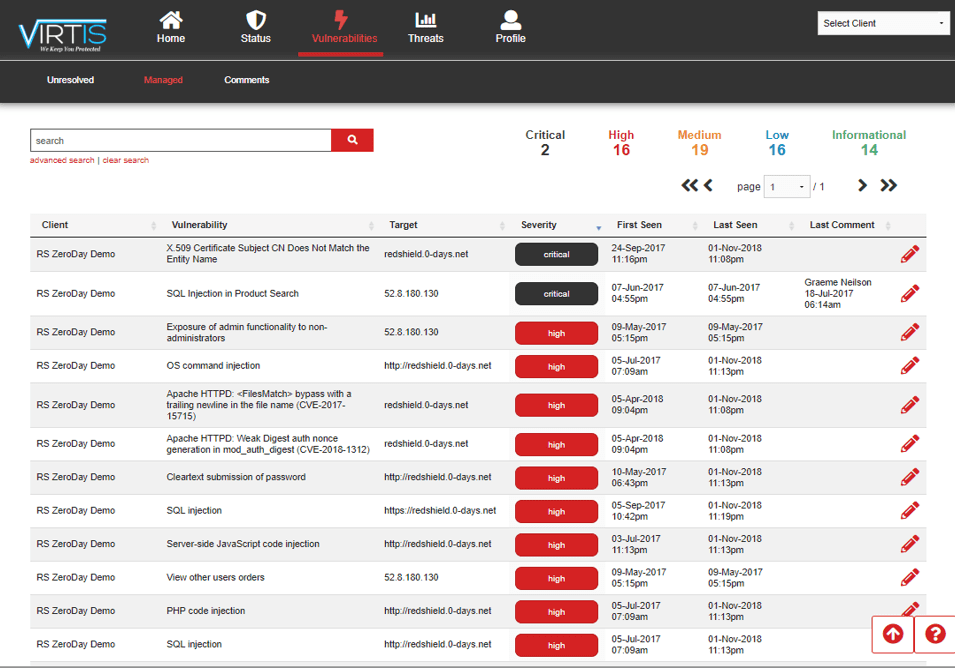
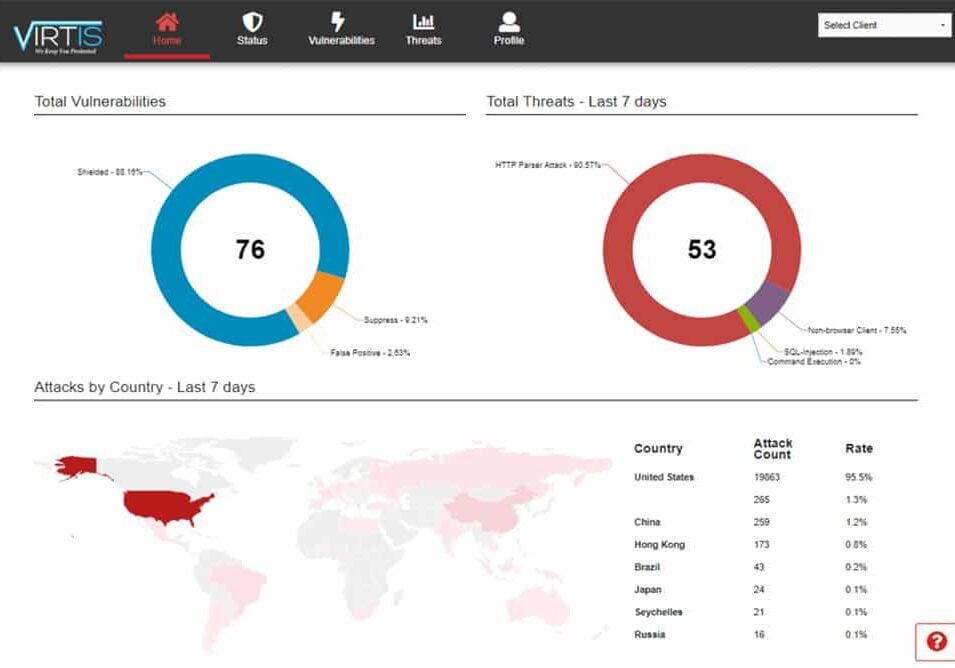
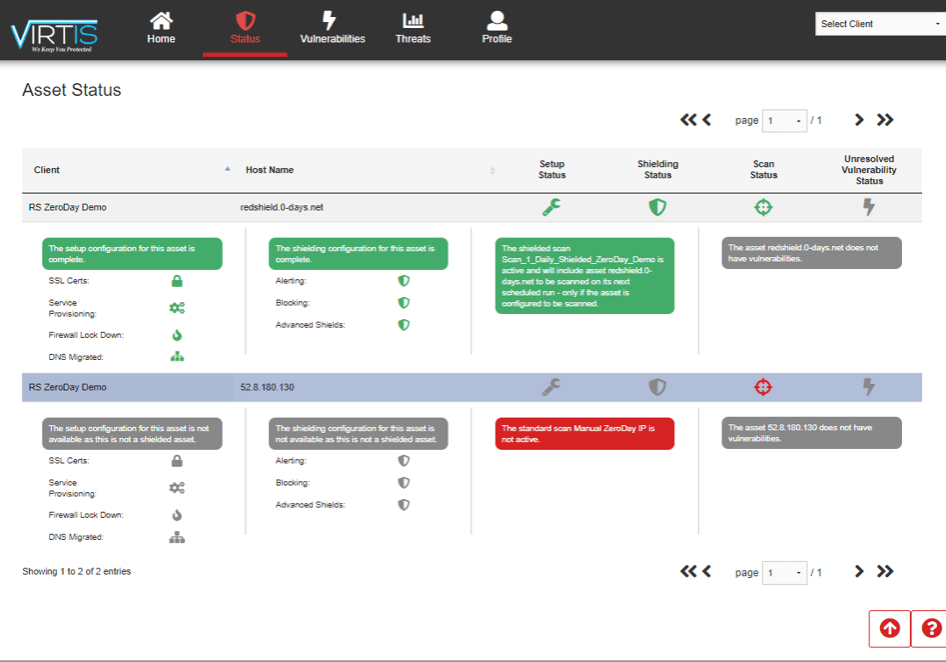
Receive a detailed Vulnerability Assessment Report to know where you are vulnerable to risk and a security plan
to immediately protect you from all of your known vulnerabilities
Click images to enlarge.
