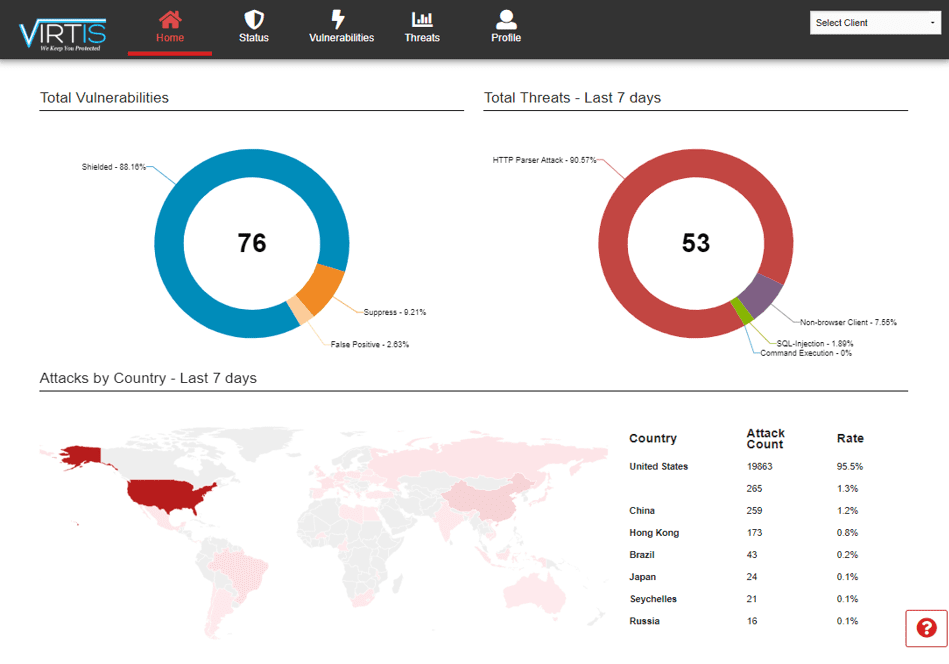
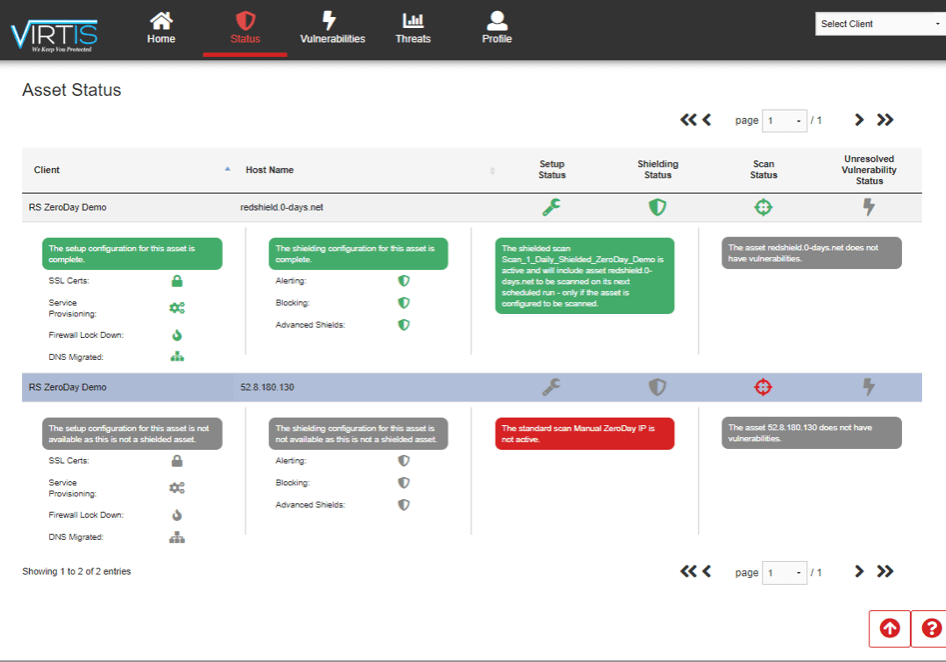
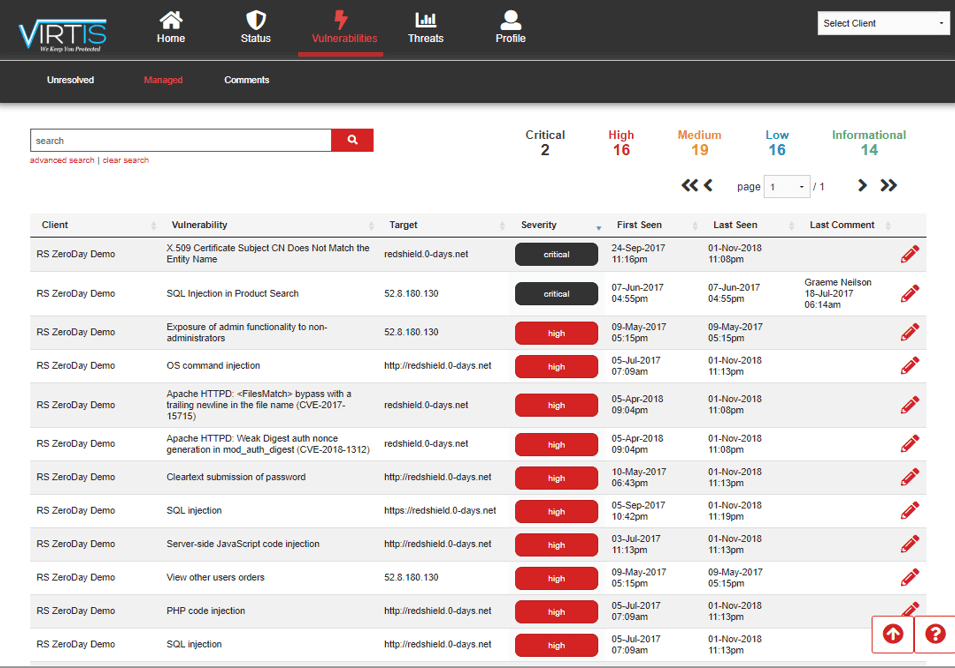
ARE YOU PROTECTED?
Every industry and every organization needs Web Application Protection (WAAP).
Whether or not an organization has:
- Outsourced their IT to a 3rd Party
- An IT/ Info Sec Dept. or Dev Ops Team
- A mature cybersecurity process
- A Security Operations Centre (SOC)
- A Chief Information Officer(CIO) and/or
Chief Information Security officer (CISO)